1.
Introdection hird-party services bring tremendous value to the web: allow websites to implement trivially first party advertising, analysis, integration of social networks, and more. But also raise privacy issues: in recent years, researchers, civil society and the authorities have drawn attention to the growing trend of third party websites recording and analyzing browsing activities of users through unrelated websites first part.
The technological part begins by surveying technologies and stateless state that can be used to correlate the activities of users on various websites. Next provides an overview of the technologies that enable the provision of third party privacy risk decreased. Finally, the user choice and self-help technologies currently available, including opt cookies, blocking, and Do Not Track is analyzed. This work is a secondary objective. Discussions on how to respond to third-party web tracking are happening every day in Washington and Brussels. We hope that through the systematization of knowledge about third party web tracking for the community of computer security and privacy, we will ensure that you are better able to assist policy makers in developing solutions that security and privacy, we will ensure that you are better able to assist policy makers in developing solutions that adequately balance privacy, trade, and a thriving network.
2. II.
3. Third-party Tracking
Many websites, especially those providing data or free content, rely on advertising to continue operations. several of these sites do not have the infrastructure for technical and business development to hire their own accounts of publishers and serve their own ads. As a result, the trust placed in different websites, third party ad serving corporations, to recruit advertisers and serve those ads on publisher sites. This arrangement allows websites to specialize in what they do best and save time and cash.
We must now how the web-site are responsible for third-parties
? First, in order to make money we force-fully advertise the ads to our own web-site. ? And in order to sell our products on the website, we are announcing our advertisements on other websites.
Because of this third we also face some problems:
III.4. Privacy Problems
This section reviews the privacy issues of persecution thirdparty internet and varying points of policy responses. Return discussion in 3 phases. First, the browsing history information is obtainable from third parties and how that information is recognizable detailed. Secondly, however explains third persecution Internet could harm users. Third, the survey results consistently show that users would like semioruga not be reviewed. Here in (Fig 1) we are able to see the ads but the third is putting on a selected site.
5. a) Information Available
Web browsing history is inextricably linked to non-public data. The pages you visit reveal their location, interests, purchases, employment standing, sexual orientation, financial challenges, edical conditions, and more. Browse loads individual pages is usually adequate to several conclusions a few user; analyzing patterns of activity permits however additional deductions. Once a page first part featuring content from third parties, the third party website is created usually attentive to the direction Computer Part page through communications protocol regarding associate degree or equivalent. T Abstract-Web is driving the evolution of the current system, allowing users to find, share and combine information websites. HTML, JavaScript and CSS no restrictions on a web page that includes elements or even delegating complete control of a fully decoupled website. These design options have contributed to a number of vulnerabilities well studied and known safety, including cross-site scripting (XSS) and cross-site request forgery (CSRF or XSRF) [1], allowing an information or perform actions on the "website first part" that the user has interacted willingly.
This article examines the privacy implications of authorizes a third party website to learn about their users.
more easily and delivery of web pages built for the content of unauthorized and unrelated "third party" web page to retrieve jurisprudence, where in front of a web site first part Publicly stated its interest knowledge phase, providing a rare insight into what others are asking supporters to find out regarding users. Segments locked biological time, getting pregnant, unhealthy credit repair and debt relief users. many months If the page includes a script tag of a third party, the third also usually will learn the title page online document. Title. Some first parties may voluntarily transmit additional data assortment including sensitive personal data is not a theoretical concern. In mid-2011 tend to discovered that advertising network associate degree, Epic market, had after I tend to find that qualitative Free online site web analytics OkCupid causality was the Lotame information provider, however usually drinks user, smoke, and the will of medicine. once Krishnamurthy et al. They tasted search queries in ten health websites fashion, found a third party learned of the user question in nine of them.
6. b) Identifiability
The third may be a first part in another context, where the user voluntarily provided its identity. Facebook, for example, has over 800 million users and enforces the requirement that users provide their real name service. When a page includes a third social Facebook widget, Facebook identifies the user to customize the widget [2]. If a website puts identification information in a URL or page title, you can unintentionally leak information to third parties. In a document of 2011, Krishnamurthy et al. Registration examined and interaction with 120 popular sites for information leakage to third parties. It was reported that a total of 48% identifier7 leaked a user in a request URI or reference. Using a similar methodology, the identification information leakage analyzed on top US Quantcast 250 websites. We could try recording and interaction with 185 sites; found that a username or user ID is sent to a domain with a different suffix public + 1 (PS + 1) 8 113 (61%) of our sample websites. The five most frequent and most prolific user name and user ID senders recipients are presented in Tables I and II respectively. In most cases the user name or user ID was part of a user profile URL or page title.
7. c) Possible Harms
The risk of harm to consumers arises web tracking possible innumerable situations. each specific state of affairs might have a chance Coffee occur. However, the prospect of some situations that happens is considerable, especially once thought about the time and most companies. After taking into account net harmful situations persecution, we found it useful to point four variables. First actor, associate degree that causes harm to a client. The possibly actor, for example, be a certified worker, malicious employee, competitor, acquirer, hacker, or office. Secondly, a form of access that allows the player to use knowledge chase. information could voluntarily transferred, sold, stolen, misplaced, or accidentally distributed. Action Thirdly, associate degree that damages the patron. The action can be, for example, publication, less favorable supply, denial of a benefit, or termination of employment. Lastly, a damage inflicted selected. The damage may be physical, psychological or economic. The countless mixtures of these variables lead to thousands of potential dangerous results for buyers. To illustrate our thinking, one usually thought-about here scenario: A hacker (actor) breaks into a search company (access) and publishes its search data (action), inflicting a shameful reality in relation to the employer to become the best known and inflict emotional distress.
8. IV.
9. Cookies
Cookie is a cute for what is basically a text file name. When you visit a website, the website can ask your web browser (like Internet Explorer or Firefox) to create a text file to store some useful information. This information can only be read by the website that created the information first. This is the concept behind Internet cookies.
When you vist a domain as www.somedomain.com, the somedomain.com server can order your browser to set a cookie. This is a cookie source, since it is determined by the domain you have chosen to visit. Party cookies are vital to many of the biggest websites. Usually they are a good thing, allowing a site to remember you entered in the system, or to remember what items you have added to your cart.
10. a) Third-party cookies
11. Global Journal of C omp uter S cience and T echnology
Volume XV Issue II Version I Year ( )
When your browser requests the image of the flag of www.anotherdomain.com, allowing the third domain to set a cookie. Each domain can only read the cookie that was created, so there should be no way to www.anotherdomain.com read the cookies created by www.somedomain.com. So what's the problem? Some people do not like third-party cookies for the following reason: assume that most Internet sites have banner ads www.anotherdomain.com. Now that the advertiser can use your third cookie to identify you as you move from one place to another place their ads with your ads. Although the advertiser www.anotherdomain.Com may not know his name, you can use the random identification number in the cookie to build an anonymous profile of the sites you visit. Then when you see the unique ID in the cookie third, you can tell yourself: "Away 3E7ETW278UT regularly visit a music site, so that he / she advertisements about music and music show products". Some people do not like the notion of advertising companies building up profiles acerca Their browsing habits, even if the profile is anonymous. ".
12. V.
13. Web Performance Today
There is a growing awareness of the fact that the third party content may cause a major blow to the performance of your site. Okay. Grande. Now we have to deal with what I have called "fourth-party calls". Not only can these insidious server calls leaching yield, they also have massive implications for safety.
You own a website and you are about a third party company to add a single line of code. We sent an implementation guide and work your developer to paste a simple code snippet. The output on page might look something like this: <iframe src = "https://secure.img-cdn.mediaplex.com/ 0/932/home_page.html? Home=0 and mpuid = Wednesday, July 13, 2011 at 16:49:10 EDT" height = "1 "width =" "frameborder =" 1 0 "> </ iframe> What happens next is the scary part: all is lost effective control.
This file starts a cascade of fourth-party calls -calls from third label you authorized to lots of other sites. You thought that with that one snippet, which had put in a single call to a server, but look at the waterfall below. Almost all of this is produced from a line that:
If you are new to reading the waterfalls, here's a quick primer. If you prefer to skip the primer, here's a quick interpretation:
? "simple" third label This led to 49 calls ? per server -requires that the site owner ? does not authorize -several fourth-party servers.
? Of these 49 calls fourth game, 21 are redirects.
(These are indicated by the red dots.) The result: a ping pong effect as each rebounds calls redirected from server to server, wasting valuable time load. ? Each of these calls quarter is over SSL, which has a significant impact on the charging time.
? What this adds up to: all these calls fourth game add 1.8 seconds to the load time of the page.
The performance impact is severe. But what really worries me is the fact that all these four partiescompanies that have no relation -are filling their databases with every last bit of information you can about your customers and your site.
14. c) Fourth-party call
What is especially troubling implications for security and privacy of calls of Game is the fact that they have unrestricted access to user data: you can view and capture all about its users without their express consent. And the kind of information we may collect is amazing Although Skechers is very happy to have the NY Times show me this announcement, my concern is that all data authorizing a third party to use to make this happen is available for any of the other fourth-party calls.
Data flowing out of the original site and in one, or perhaps even many, databases, scary. Want the entire browsing history of users, including what products you looked at your site, collected and sold by strangers?
Worse, perhaps, is that the fourth-party calls may change at any time at the whim of the third part -or even another fourth game -as many of these call cascade and delivered from one company to another.
People routinely in a stew every time Facebook changes its privacy settings, but at least the Facebook privacy settings are something that can be controlled via a dashboard. If people knew how much of their personal navigation history has already been captured and stored in a number of databases, the protest could stifle complaints related to Facebook.
15. VI.
16. Advantages
? Measurement of third-party content can pinpoint whose domain is responsible for the poor performance. ? Further analysis may allow content management under their ownership.
? It is easier to monitor ongoing performance of all content, whether inside or third. ? The specific alarms in case of a drop in performance can lead to a quicker resolution of potential problems. ? Specific tests and associated alarms can help improve development practices, as some performance problems are due to erroneous modifications of previously working code. ? Performance monitoring selective third party content may establish proof of the liability of third party vendors. This may also establish accountability for performance problems that slow or block the Web site. VII.
17. Do not Track
Do Not Track is a proposal technology and policy that allows users to opt out of tracking by websites that are not visited, including analysis services [11], advertising networks, and social platforms. Today some of these third parties offer reliable opt out monitoring, and tools for blocking them are easy to use nor nor complete. Like the popular not call, Do Not Track provides users with a single option, simple and persistent to opt out of third party web tracking. Do Not Track signals opt-out preference of a user with an HTTP header, a simple technology that is fully compatible with the existing network. While some third parties have pledged to honor Do Not Track, many more do not. In February 2012, major trade groups online advertising pledged at the White House to support Do Not Track end of the year; that promise remains unfulfilled. Efforts to standardize Do Not Track in the Consortium of the World Wide Web have resulted in a stalemate, despite frequent urge Americans and Europeanpolicymakers.
We do not track that could be a success, but at this time, must be implemented through either a legal or technical requirement. Meanwhile, new technical countermeasures as Cookie-Clearinghouse promising options to provide simple and effective user web tracking.
18. VIII.
19. Conclusion
This paper surveyed and technology policy issues in the thirdparty web crawling principles. The field is changing rapidly; new ads, questions and research results appear in the week. We hope the information presented here provides researchers security and privacy with the necessary background to contribute to this developing field and participate meaningfully in public debate.
20. Year ( )

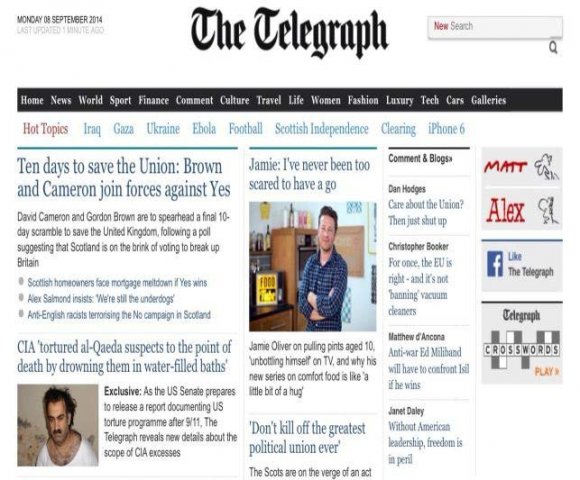
![[8]. Here's a fairly innocuous example (Fig2). A few months ago, I went to the artists website: A while later, I was visiting the site of the New York Times. Note the ad in the lower right corner in (fig 3): Global Journal of C omp uter S cience and T echnology Volume XV Issue II Version I Year ( ) b) Single third-party call](https://computerresearch.org/index.php/computer/article/download/1148/version/100944/5-Third-Party-Web-Advertisements_html/16590/image-4.png)