1. I. INTRODUCTION
ireless Sensor Network consists of no. of sensor nodes where nodes are deployed in a region to monitor its environment. Each sensor nodes consists of Microcontroller, internal & external memory, antennas, sensor and batteries as its main components to perform a specific task. Each sensor node senses its input attributes process the raw data & converts it into digital data format and then forward the data through chain of network using optimized routing scheme till the data reaches to its correct destination.
When the data is travelling through optimized routing path then there are chances of data packet to compromise from its authenticity, confidentiality, and integrity before it reaches to the destination. Therefore to overcome such threats which may exist in WSN depending on its application, there is requirement of strong cryptographic technique to counter. Wireless sensor nodes resources have its own constrained in terms of limited computational speed & battery backup. There exist plenty of energy efficient secure & routing algorithms such as LEACH, PEGASIS, TEEN, APTEEN, GBDD, TTDD, DES, AES, RSA, DSA, Elgamal encryption etc has achieved appreciable popularity for improved performance efficiency. However all the existing protocol has its own limitations and their drawbacks which has been studied & analyzed in detail for further research improvement & development in the field of wireless sensor networks.
Wireless Data Communication poses some kind of threats due to its open environment communication.
To avoid compromise of data security it is required to maintain the authenticity, confidentiality and integrity of data. The elliptical curve cryptosystem provide speedy security mechanism compare to other type of public key cryptosystem and used in constrained environment conditions. Elliptical Curve Cryptography provides advantage of smaller key size that result in to faster computations, lower power consumption with savings of memory and bandwidth that makes ECC a fast, flexible, low cost security algorithm suitable for constrained environment.
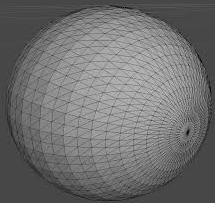
Wireless Sensor Network can be deployed for Tele communication connectivity between various regions of all over the world. The modeling and placement of Wireless sensor nodes across various parts of world region for the coverage of whole world forms a cluster of networks which appears into spherical shape as shown in figure-1. The WSN find applications in,
2. WSN SECURITY & ROUTING: A REVIEW
In cryptography the plaintext message content before it is sent out over the infrastructure network is encrypted, which becomes the cipher-text. At the destination side in order to read the plaintext, the ciphertext has to be decrypted. The application of wireless sensor network is wide spreading. The WSN are having limited power source, which required an ultimate power efficient routing and security protocol. There are several asymmetric cryptography schemes that are used to provide the security services. The Elliptic Curve Cryptography (ECC) performance is better for low power implementation applications.
To ensure the communication network function correctly and safely, there are mainly four security requirements of WSN i.e. Authenticity, Integrity, Confidentiality, Availability.
In Wireless communication routing path is set up by establishing in either of three ways namely reactive, proactive and hybrid. Reactive protocols decide the routing path when they are ready with information to transmit. Proactive protocols calculate all the routes in advance and maintain the records in a routing table of each sensor node. If there is change in the route, the changes is updated throughout the network and due to this region proactive protocol are not suitable for WSN. Hybrid protocols join the idea of proactive and reactive protocols. Some of the routing protocols are discussed below.
Hierarchical protocols: Such protocols are suitable for higher scalability. Hierarchical protocols functions in two tier, first tier is used to decide about cluster-heads and the other tier is used for data routing. This protocol is more energy efficient and improves network scalability, lifetime and quality of service.
Location based Protocols: This protocol used nodes location information to decide the closeness among two or more nodes to estimate the energy consumptions. Two methods are used to determine the sensor node location, first one which calculates the coordinates of the neighbouring node and second one uses the global positioning system.
Ad-hoc on demand distance vector (AODV) Protocol: AODV is the energy efficient and shortest path routing algorithm widely being used for wireless network. It uses methods of path discovery and maintenance. AODV form routes between sensor nodes only when they are needed.
3. III. ELLIPTICAL CURVE CRYPTOGRAPHY
Elliptical Curve Cryptography (ECC) is suited for WSN applications. The benefit of this technique is that they uses smaller size key which need less storage, less bandwidth and less energy, thereby reducing processing and communication overhead, which is ideal for energy-constrained sensor nodes. An elliptic curve is the points in the x-y plane that satisfy an algebraic equation y 2
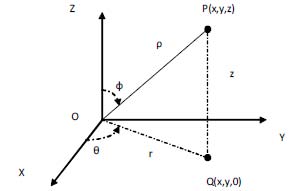
4. Spherical Coordinates:
In the spherical coordinate system, as shown in figure 5 a point P(x, y, z) whose Cartesian coordinates are (x, y, z), is described by an ordered triple (?, ?, ?), where ? > 0, 0? ? ? 2?, 0? ? ? ? are defined as follows.
? ? = dist(P, O) ? ? is defined as the angle from zx-plane, counterclockwise, to the half-plane originating from z-axis and containing P. ? ? = angle from positive z -axis to vector ???? ??????
5. : Spherical Cartesian System
Note that when P is on z -axis, ? = 0, and ? increases from 0 to The coordinate system formation of the spherical grids is shown in figure 6.
6 : A Spherical Grid V.6. ELLIPTICAL CURVE BASED MULTI-TIER SPHERICAL GRID ROUTING (ECMSGR): A PROPOSED METHOD
The several sensor nodes are uniformly distributed across a field to form wireless sensor network for the secure routing of data packet between source and destination. Each sensor node senses its input attribute and before its send the data packet to its neighbor node it forms a routing path in spherical grid fashion with proper coordination among no. of sensor nodes. For the uniform utilization of sensor nodes, each sensor node is checked for remains energy level and no. of times used for path formation by the neighbouring sensor node as shown in figure . In WSN multi-tier spherical grid routing path formation between two or more sensor node is calculated by determining previous and next sensor node angular position such that path formation will be in spherical fashion between starting node and destination node as shown in figure 7. Source as indication in figure 7 is sensed by a sensor node near to it. The sensed node now decides about choosing second next node with required angle and second node select third node such that the routing path formation between source and destination takes spherical shape. The red dot represent one tier spherical grid and blue dot represent second tier and so on routing path formation takes place.
The required angular position between nodes formation is shown in figure 8. The elliptical curve based multi-tier formation of spherical grid routing to cover very large area with effective & optimized utilization of sensor node is represented by figure 9.
7. VI. RESULTS & DISCUSSIONS
The Proposed protocol ECMSGR is compared with LEACH and GRID protocol in network simulator 2 environment to evaluate the performance metric such packet delivery ratio, throughput, communication overhead, end-end delay and power consumption. The table I represent simulation parameter set up for NS2. A large area is covered by a large number of sensor nodes which communicate with each other through short-range radios. Long-range data delivery is achieved by forwarding data across multiple hops. Each sensor is aware of its own location. However, mobile sinks may or may not know their own locations. When a stimulus appears, the sensors surrounding it collectively process the signal and one of them becomes the source to generate data reports. Sinks (users) query the network to collect sensing data. There can be multiple sinks moving around in the sensor field and the number of sinks may vary over time as shown in figure 11.
8. Conclusion
The proposed method ECMSGR provides a novel and an approach towards improvising potential WSN performance specially in terms of packet delivery ratio, throughput, communication overhead, end-end delay and power consumption. The network route formation as well as data transmission and its security are a major concern in the field of wireless sensor network. The ECMSGR protocol implementation and its performance compare to other related protocol is designed and analyzed to overcome some of the limitations of existing protocol using network simulator-2. The experimentation scenario and results shows that ECMSGR outperforms GBDD & M-LEACH. The ECMSGR protocol complexity increases when the network scalability increases at very large scale in the application of providing smart & secure gobal communication for data as well as voice communication to end users. ECC offer advantages of higher speeds, lower power consumption, and code size reductions. This concludes that ECC is best suited for wireless applications which demands speed, time and bandwidth. The results shows that optimal key generation time, encryption time and throughput using simulation. In this paper ECMSGR protocol gives an idea for researcher to explore further possible performance efficiency enhancement to offer better quality of services to provide communication coverage across globe.

| Simulation Parameters | Value |
| Channel type | Wireless Channel |
| Radio-propagation model | Propagation/Two Ray Ground |
| Network interface type | Phy /WirelessPhy |
| MAC type | Mac/802_11 |
| Interface queue type | Queue/DropTail /PriQueue |
| Link layer type | LL |
| Antenna model | Antenna/Omni Antenna |
| Max packet in IFQ | 50 |
| Number of mobile nodes | 16/25/36/49/98/196 |
| Routing protocol | AODV/DSR/DSDV |
| X dimension of topography 4000 | |
| Y dimension of topography 4000 | |
| Time of simulation end | 20/40/60/80/100 |
| Initial energy in Joules | 100 |
| Network Type | Mobile |
| Connection Pattern | Random |
| Packet Size | 512 bytes |
| Connection type | CBR/UDP/TCP |