1. Introduction
mobile ad hoc network (MANET) is an interconnected system of mobile hosts without a fixed infrastructure. Every node in an MANET must be able to function as a route to forward data to other nodes. When applications must send the same data to more than one destination, multicasting is often used. Multicasting reduces the communication costs for applications that send the same data to multiple recipients. Instead of sending via multiple unicast, multicasting minimizes the link bandwidth consumption, router processing and delivery delay .Existing multicast routing protocols for MANETs can be broadly classified into tree-based routing protocols [1][2][3][4][5][6][7][8][9] and mesh-based routing protocols [10][11][12][13][14][15]. Tree-based routing protocols build a tree structure that connects all multicast members and provide one path between a pair of source and destination nodes.
Mesh-based protocols yield a multi-path between the source and the destination nodes. When a link fails, mesh-based multicast protocols do not need to re-compute a mesh. Royer and Perkins [7] propose a multicast ad hoc on demand distance vector routing Authors ? ? : Guru Nanak Dev Engineering College Bidar Karnataka, India. E-mails : [email protected], [email protected] protocol (MAODV). MAODV establishes on-demand multicast tree and uses these for delivery of multicast data. MAODV is a typical tree-based multicast routing protocols. Ballaradie, A., Crowcroft J., Francis [3] proposed a new protocol called MQ, Multicast with QoS, which supports multimedia group communications with QoS guarantees for heterogeneous recipients. With MQ, while resource reservation is de-coupled from QoS multicast routing, they are integrated in a way to avoid the problem of sender-oriented path determination, a problem that occurs when RSVP is used in conjunction with QoS routing for heterogeneous reservations. Bommaiah, E .and McAuley, A [5]propose a multicast routing protocol for ad-hoc networks, which is particularly efficient for multi-source multicast transmissions. In order to minimize the total transmission power in MANETs, routing protocols have been proposed to increase the lifetime of networks [16 -18].Minimum total transmission power (MTPR) [17] establishes on-demand unicast routing based on the transmission power. This paper is discussed in following number of section. Section II deals Ad-hoc wireless network, Section III deals with Routing protocol. Section IV Wireless Simulation, Section V deals with Simulation Results, Section VI deals with conclusion and section VII deals with References.
2. II.
3. Adhoc Wireless Network
A mobile Adhoc network is a collection of wireless mobile nodes that communicate with one another without any fixed networking infrastructure. Ad Hoc networks are multi-hop wireless networks where all nodes cooperatively maintain network connectivity. These types of networks are useful in any situation where temporary network connectivity is needed, such as in disaster relief. In multi-hop wireless ad-hoc networks, designing energy-efficient routing protocols is important because nodes have limited power. However, it is also an inherently hard problem due to two important factors: First, the nodes may be mobile, this requires that the energy-efficient routing protocol should be fully distributed and adaptive to the current states of nodes; Second, the wireless links may be uni-directional due to asymmetric power configurations of adjacent nodes.
4. Routing Protocol
Ad hoc Routing protocols is classified into two types such as proactive and reactive. The table-driven routing protocol is proactive, it worked on distance vector based or link state based routing strategies. The drawback of this algorithm is the frequent updation is required which consumes large amount of memory, bandwidth and power [31]. But, in the reactive routing protocol, each node does not need to maintain the routing table. When a source node is ready to send data, it initiates the route discovery procedure and maintains its routes only. The reactive routing protocol minimizes the routing overhead and also called on-demand approach.
5. a) AODV Protocol
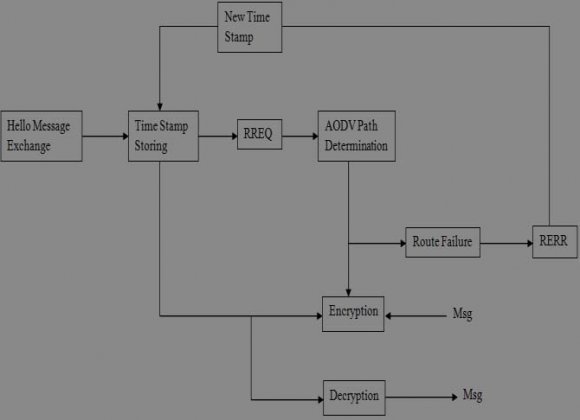
The AODV [32] protocol based on the reactive routing discovery uses three different kinds of messages: Route request (RREQ), Route Reply (RREP) and Route Error (RERR). In addition, destination sequence numbers are used to ensure loop freedom at all times. In AODV, each source node finds a new route by the limited flooding of RREQ and obtains a route to its destination through RREP. b) AOMDV Protocol AOMDV [33] uses the basic AODV route construction process. In this case, however, some extensions are made to create multiple loop-free, linkdisjoint paths. The main idea in AOMDV is to compute multiple paths during route discovery. It consists of two components:
1. A route update rule to establish and maintain multiple loop-free paths at each node. 2. A distributed protocol to find link-disjoint paths.
Before describing AOMDV, we first discuss AODV, from which it is derived. In AODV, when a source needs a route to a destination, it initiates a route discovery process by flooding a RREQ for destination throughout the network. RREQs should be uniquely identified by a sequence number so that duplicates can be recognized and discarded. Upon receiving a nonduplicate RREQ, an intermediate node records previous hop and checks whether there is a valid and fresh route entry to the destination in routing table. If such is the case, the node sends back a RREP to the source; if not it rebroadcasts the RREQ. A node updates its routing information and propagates the RREP upon receiving further RREPs only if a RREP contains either a larger destination sequence number (fresher) or a shorter route found. In AOMDV each RREQ, respectively RREP arriving at a node potentially defines an alternate path to the source or destination. Just accepting all such copies will lead to the formation of routing loops. In order to eliminate any possibility of loops, the advertised hop count is introduced. The advertised hop count of a node i for a destination d represents the maximum hop count of the multiple paths for d available at i. The protocol only accepts alternate routes with hop count lower than the advertised hop count, alternate routes with higher or the same hop count are discarded. The advertised hop count mechanism [33] establishes multiple loop-free paths at every node. These paths still need to be disjoint. Duplicate copies of a RREQ are not immediately discarded. Each packet is examined to see if it provides a node disjoint path to the source. For node-disjoint paths all RREQs need to arrive via different neighbors of the source. This is verified with the first hop field in the RREQ packet and the first hop list for the RREQ packets at the node. At the destination a slightly different approach is used, the paths determined there are link-disjoint, not node disjoint. In order to do this, the destination replies up to k copies of the RREQ, regardless of the first hops. The RREQs only need to arrive via unique neighbors. c) Enhancement in Network Life time using binary tree based multicast routing protocol for mobile ad hoc network
In this study, a Enhanced Network Life Time tree-based multicast routing protocol (NLDTMRP) for MANETs is proposed. In the proposed scheme, all nodes are randomly classified into two types, group-1 and group-2. To achieve the load balance, two multicast trees (tree-1 for group-1 and tree-2 for group-2) are constructed .Each node maintained two routing tables: the neighbouring table and the routing table. The neighbouring table was easily obtained by the periodic broadcast of the hello packet. These tables are described below:
1. Neighbouring The src ID and Dest ID fields contains the unique addresses of the source and the destination node, respectively. The seqno field contains the sequence number of the source node (guaranteeing the loop-freedom of all routes to the destination node). The route_class field recorded the class of route for group-1 or group-2. The next_hop field contained the address of the neighbouring node to which data packets had to be forwarded. In the proposed scheme, power level threshold (P threshold ) is defined. When the source node wants to send the packet to the destination nodes, it broadcasts the route request (RREQ) packet to the neighbouring nodes in its transmission range, when the source node does not have a path in the routing table. The RREQ packet carries the following information in its header: 'Type' refers to the packet type: RREQ, RREP or RERR. 'Src' is the source node. 'SrcSeq' is a monotonically increasing sequence number. 'Src' and 'SrcSeq' are used to uniquely identify each RREQ packet. It can be used to check duplicate copies of an old request and detect the stale cached routes. 'DestList' is a set of destinations. 'Path Traversed' Here 'Type' is certainly RREP. 'Source' is the source node. 'Destination' is the destination node. The field 'ReversePath' in each RREP packet includes the reverse path. 'Class' is the type of node: group-1 or group-2.The Class field of RREP packet is the assigned type for the RREQ packet. When the intermediate node receives the RREP packet, it selects the upstream node based on the corresponding type of RREP packet and sends the RREP packets to the source node. The detail of the route discovery process.
6. i. Algorithm 1: Route discovery process
A n etwork is modeled as graph G(N, E), where N is the finite set of mobile nodes and E is a set of links. Suppose n is the number of mobile nodes and N is the set of mobile nodes N= {N1, N2, . . . , Nn}
7. Route Maintenance Process
It is divided in to three parts: i. Join Operation When a new member wants to join the multicast tree, it broadcasts a join route request (RREQJ) packet across the networks. Only a node that is a member of the multicast tree (i.e. a router for the group) may respond, if a node receives a RREQJ packet for a multicast group of which it is not a member or it does not have a route to that group, it creates a reverse route entry to the prospective node and then broadcasts the RREQJ packet to its neighbours. Any intermediate node receives the RREQJ, it rebroadcasts the RREQJ if the P remain of the node is higher than P threshold . When each member node of the multicast tree receives the RREQJ ii. Node Prune Operation When a node wants to move from the multicast tree, the pruning node broadcasts to its upstream node a pruning route request (RREQP) packet. When the upstream node receives the RREQP packet, it removes the corresponding entry from its multicast routing table. If the upstream node becomes a leaf node and it is not the tree receiver, the node can further prune itself from the tree. records the routing information. "Class" is the type of node: group-1 or group-2. "RREQType" refers to the RREQ type: RREQ, After neighbouring nodes receive the RREQ packet, the neighbouring nodes first check the remaining battery of nodes (P remain ). When P remain of nodes is higher than P threshold , the neighbouring nodes store received the RREQ packet and re-broadcasted the RREQ packet. The neighbouring node adds its ID to the routing path field of the RREQ packet and the class field of the RREQ packet is assigned a type (group-1 or group-2) of neighbouring node. When the destination node receives the first RREQ packet with group-1 and the first RREQ packet with group-2, the destination node selects the last hop of each RREQ packet as its upstream node to be the primary routing paths for tree-0 and tree-1. Then, the destination node sent two route reply (RREP) packets to the source node. The RREP packet carries the following information in its header: iii. Broken Link Maintenance
In NLTMRP, when a node fails to deliver the data packet to the next hop of the route, it considers the link to be broken and sends a route error (RERR) packet to the source node. When the upstream node receives the RERR packet, it removes the corresponding entry from its routing table and forwards the RERR packet to the source node. If only one of the two routes is broken, the source uses the remaining valid route to deliver data packets. When both routes of the path are broken, the source node initiates the route discovery process. The RERR packet carries the following information in its header: a. Aglorithm2
8. Node Ni continues packet transmission. } else
The simulation was implemented by using NS2 (Network Simulation 2, version 2.35) [30]. The simulation modeled a network in a 900 m × 900 m area with varying mobile speed. We used random waypoint model was used as mobility model. In random waypoint model, each node randomly selects the moving direction, and when it reaches to the boundary of simulation area, it bounces back and continues to move. The transmission range was 150 m. The data packet size was 250 bytes. The initial power of each node was 10 J. P threshold was 0.5J. Each simulation was executed for 600sec. The source and destination nodes were randomly chosen and each node was randomly assigned an initial energy. We used constant bit rate (CBR) as the traffic type. In CBR model, the source transmits a certain number of fixed size packets. The parameters used in the simulations are listed as shown below. The performance evaluation metrics used in the simulations were:
9. Packet Delivery Ratio
The data packets delivered divided by the data packets expected to be delivered.
10. Control Overhead
The control packets transmitted divided by the data packets delivered.
11. Packet Delivery Delay
The interval from the time the multicast is initiated to the time the last host finishes its multicasting.
12. Total Energy Consumption
The total consumed Energy of all nodes after data transmission.
13. Network Lifetime
The duration of the network operation time until the first node failure because of battery depletion at the node.
IV.
14. Wireless Simulation
The Network simulation-2 implementation has following important parts. T time out seconds, and waits for the repair route reply (RREPR) packet to return. The simulation was implemented by using NS2 (Network Simulation 2, version 2.35) [30]. The simulation modeled a network in a 900 m × 900 m area with 50 mobile nodes. We used random way point model was used as mobility model. In random waypoint model, each node randomly selects the moving direction, and when it reaches to the boundary of simulation area, it bounces back and continues to move. The mobile speed of each node was from 1 to 25 m/s. The transmission range was 150 m. The data packet size was 250 bytes. The initial energy of each node was 10 J. P(threshold) was 0.15J . Each simulation was executed for 600s. The value in the following simulation figures are the average values of 50 runs. The source and destination nodes were randomly chosen and each node was randomly assigned an initial energy. We used constant bit rate (CBR) as the traffic type.
V.
15. Simulation Results
In the following, the impact of mobility speed on AODV, AOMDV and NLTMRP is studied. These protocols have been simulated for packet delivery ratio, packet delivery delay, total energy consumption and Network Life Time.
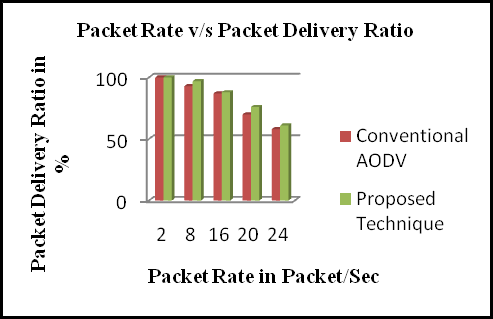
From Figs. 2-5, we depict the routing performance of three protocols under different mobility speeds. Fig. 2 shows the performance of the packet delivery ratio under various mobility speeds. As shown in Fig. 2, the packet delivery ratio decreased with increasing mobility because of more link breaks. Notice that the packet delivery ratio is high when the nodes have low mobility. NLTMRP achieves a much higher packet delivery ratio than AOMDV and AODV because energy is evaluated while establishing of two stable routing paths for multicasting. Thus, the packet delivery ratio of NLTMRP is higher than that of AOMDV and AODV protocol.
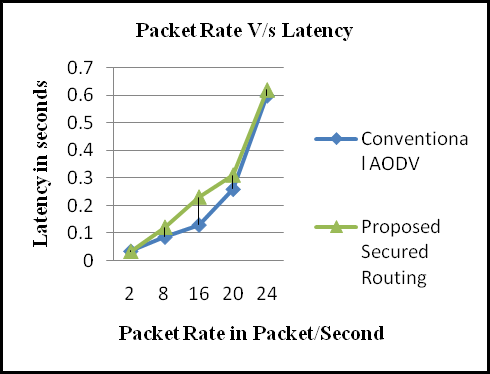
From Fig. 3 we depict performance of the packet delivery delay under various mobility speeds. As shown in Fig. 3, as the mobility speed increases, the packet delivery delay also increases. The packet delivery delay of NLTMRP is lower AOMDV and AODV. This is also because energy is evaluated while establishing of two stable routing paths for multicasting.
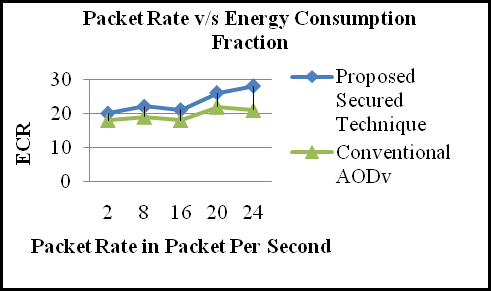
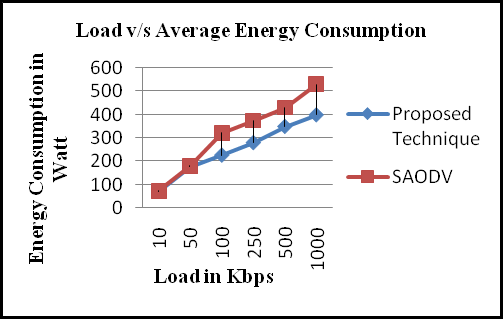
From Fig. 4, shows the performance of the total energy consumption energy under various mobility speeds. Owing to the mobility of the node making the control overhead increases, it consumes more energy. Therefore the total energy consumption increases with increasing mobility. As observed in Fig. 4, the total energy consumption of NLTMRP is lower than that of AOMDV and AODV. This is because of NLTMRP reducing the energy consumption by using dual trees for transmission.
Fig. 5 shows the performance of the control overhead under various mobility speeds. As is expected, the control overhead increases as the mobile nodes became more mobile. The reason is that there are more chances for routes to break when the speed of the mobile nodes is faster. Thus, the number of rebroadcasts increased. NLTMRP not only eliminates inefficient nodes to decrease the number of control packets, but also structures dual trees to reduce the number of route reconstructions. Therefore NLTMRP has a lower control overhead than AOMDV and AODV protocol.
From Fig. 6 shows the performance of the network lifetime at various mobility speeds. From this figure, the network lifetime of NLTMRP outperforms that of AOMDV and AODV. This is because the node residual battery power of NLTMRP is always higher than that of AOMDV and AODV.
16. Conclusion
In this paper, we propose a NLTMRP for MANETs. In this scheme, load balance is used to increase the lifetime of a network. In the route discovery, this scheme not only improves the route stability of multicast routing, but also achieves the load balance of data transmission. Therefore the control overhead for route construction and the number of route reconstructions can be decreased. Simulation results show that the packet delivery ratio and the packet delivery delay of the proposed scheme outperform that of AOMDV and AODV. Moreover, the traffic load can be balanced and the network lifetime can be prolonged. NLTMRP is a energy-aware multicast routing protocol. The node with low energy does not selected as a member of multicast tree. NLTMRP improves the route

![network is modeled as graph G=(N, E), where N is the finite set of mobile nodes and E is a set of links. Suppose n is the number of mobile nodes and N is the set of mobile nodes N ={N1 , N2 , .. . , Nn}. Assume that node Ni wants to send a packet to node Nj, where Ni, Nj, [ N, 1 <= i, j<= n, i = j ]and that the link between node Ni and node Nj breaks. if (the link of node Ni to node Nj breaks) 1. Node Ni saves the current data packet. 2. Node Ni broadcasts a repair route request (RREQR) packet to node Nj , counts down If (the RREPR packet is back in T time out seconds) { 1. Node Ni uses the replacement path to replace the path that breaks.](https://computerresearch.org/index.php/computer/article/download/186/version/100730/3-Enhancement-of-Network-Life_html/12197/image-3.png)
| Nodeid Distance |
| 2. Routing Table : This table contained the path that |
| was used for the transmission of data. The format |
| of the path table was |
| Src ID DestID Seqno Routeclass Next_hop |
| Simulator | Ns-2.35 |
| Routing Protocol | AODV, AOMDV, NLTMRP |
| Simulation Time | 600sec |
| Number of Nodes 100 | |
| Mobility peed(m/s) 1-25 m/s | |
| Mobility Model | Random way point Model |
| Simulation Area | 900 X 900 |
| Node transmission | 150 m |
| Range | |
| Data packet Size | 250 bytes |
| Traffic Type | CBR |