1.
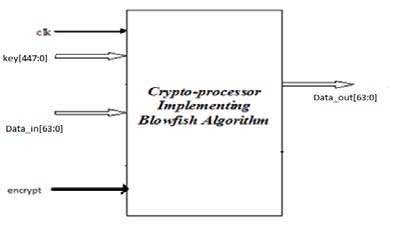
In the evaluation phase, each input signal is differential and the WDDL gate calculates its differential output. In the precharge phase, the inputs to the WDDL gate are set at 0. This puts the output of the gate at 0. During the precharge phase, the input vector of the combinatorial logic is set at all 0s. Each individual gate will eventually have all its inputs at 0, evaluate its output to 0, and pass this 0 value to the next gate. One could say that the precharge signal travels over the combinatorial logic as a 0-wave, hence, WDDL. They produce an all-zero output in the precharge phase (clk-signal high) but they produce actual logic when they it is let the differential signal through during the evaluation phase (clk-signal low). Comparing symmetric key algorithms, BF algorithm is fast, more secure with large key size and its chosen as choice of cryptographic algorithm to implement secure ICs against Differential Power Analysis (DPA) attack [10,11] using Wave Dynamic Differential Logic (WDDL).
In fig no.3, when clock is precharge mode (high), output is zero for both. When clock is evaluation mode (low), outputs are complemented and worked as XOR and XNOR.
2. b) Blowfish Algorithm
Blowfish is a 64-bit block cipher [1,2] presented by Bruce Schneider and is a suggested replacement for DES (Data Encryption Standard). DES was the standard cryptographic algorithm for more than 19 years, but it is now accepted that its key size is too small for present usage. It has a variable-length key block cipher of up to 448 bits. Although a complex initialization phase is required, the encryption of data is very efficient. It suits applications where the key does not change often.
WDDL can be implemented for any logic design. Since the discussion moves around crypto processors, it would be wise to consider a cryptographic algorithm called Blowfish is a fast algorithm [3,8].
3. II.
4. Analysis of Blowfish Algorithm
5. b) Substitution Boxes (S-boxes)
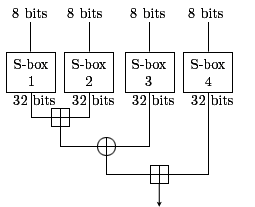
A substitution box (or S-box) is a basic component of symmetric key algorithm used to obscure the relationship between the plaintext and the cipher text In general, an S-box takes some number of input bits, 8_bit, and transforms them into some number of output bits, 32_bit: an 8×32 S-box, implemented as a lookup table [1,3,8] c) Feistel Function Block
6. d) Modulo 32-bit adder
To increase the speed of blowfish adders in this fig no.8 can be operated in parallel. one adder adds Two h-bit residues, X and Y to form their sum S1+2hCout1 .Another one is 3-operand adder that computes "X+Y+m". Note that if m=2n+1, we have h=n+1.It has been reported that if either Cout1 or Cout2 of this addition is '1' then the output is X+Y+m instead of X+Y. However, in the following we illustrate that only if the carry of "X+Y+m" is '1', it is sufficient to select it as the final output [4,9] The sub-key generation unit expands the given 448-bit key into 14 sub-keys and 4 more subkeys are internally generated, each of 32 bits, so that they can be used at different stages in the algorithm. The sub key generation process is designed to preserve the entire entropy of the key and to distribute that entropy uniformly throughout the sub keys. It is also designed to distribute the set of allowed sub keys randomly throughout the domain of possible sub keys. Then bit wise XOR of the P-array and K-array is performed reusing the words from K-array as needed shown in equation no.3. P 1 = P 1 ^ K ? P 14 = P 14 ^ K 14 P 15 = P 15 ^ K 1 ? P 18 = P 18 ^ K 4 -
IV.
7. Results and Discussion
Encryption consists of sixteen rounds of operations. Each round-one operation consists of xor, 8-Volume XIII Issue XVII Version I The encryption and decryption modules are integrated in the top level module to obtain the blowfish crypto-processor and the simulation results are analyzed.
Blowfish Algorithm is implemented in four forms and compared its performance parameters which are given below in the table no.1 and the modified blowfish is producing better results than the normal blowfish. Analysis is done for blowfish with and without WDDL logic to secure the ICs against DPA attack by the hackers.
Comparison of Blowfish, modified Blowfish with and without WDDL logic is given below in the table no.1 and the corresponding bar charts are shown in the fig no.9, 10 and 11 for performance parameters Et, Dt and Tt respectively. Et: Encrypt Time, Dt: Decrypt Time, Tt: Total Time
8. Conclusion
In this paper, an implementation of Blowfish Algorithm is designed using WDDL Logic style. In the implementation bottom-up approach is used. The subkeys generated for a particular key can be used for the encryption of the entire data to be encrypted with that key. The sub keys are given in reverse direction of the decryption data path without changing the design for decryption. The crypto processor has been designed for the key size of 448 bits and plain text of 64 bits. The code for the implementation has been written in Verilog HDL. The functional verification has been done using the ModelSim 5.

![Figure 7 : Function Block Internal Structure Function 'F' is used to create 'confusion' to thwart cryptanalysis based on statistical analysis. 'Confusion' seeks to make the relationship between the statistics of the cipher text and the value of encryption key as complex as possible. One advantage of this model is that the round function F does not have to be invertible, and can be very complex as shown in fig no.7 [1, 3, 8].](https://computerresearch.org/index.php/computer/article/download/29/version/100767/1-Performance-Analysis-of-Secure_html/12906/image-7.png)
![Year bit to 32-bit substitution, 32-bit modulo addition, xor, 32bit modulo addition and swapping of result of Left Encryption (LE) to Right side and Right Encryption (RE) to left side of the data flow as shown in fig no.6. After performing 16 round-one operations right side output[31:0] xored with subkey p16[31:0] and left hand side output[31:0] xored with subkey p17[31:0] and then we get final cipher text[63:0]. Decryption is same as that of encryption except we applied subkeys p0 to p17 in reverse order. Input data is the ciphertext (output of encryption) and then we get the output as Plaintext. Decryption consists of sixteen-round one operation. Each round-one operation consists of xor, 8-bit to 32-bit substitution, 32-bit modulo addition, xor, 32-bit modulo addition and swapping of result of Left Encryption (LE) to Right side and Right Encryption (RE) to left side of the data flow as shown in fig no.7. The input data ciphertext[63:0] performs 16 round-one operations with 16 sub keys(p17 to 2) and then after performing 16 round-one operations right side output[31:0] xored with subkey p1[31:0] and left hand side output[31:0] xored with subkey p0[31:0] and then we get final plaintext.](https://computerresearch.org/index.php/computer/article/download/29/version/100767/1-Performance-Analysis-of-Secure_html/12908/image-9.png)
| S | Name of Crypt- | Performance parameters | ||
| No | algorithm | Et(ns) | Dt(ns) | Tt(ns) |
| 1 | Blowfish | 98.663 | 98.663 | 99.395 |
| 2 | Modified Blowfish | 70.08 | 70.08 | 71.067 |
| 3 | Blowfish with WDDL 107.62 | 107.62 | 112.56 | |
| 4 | Modified Blowfish | 73.985 | 73.985 | 76.337 |
| with WDDL | ||||