1. INTRODUCTION
mobile ad hoc ne twork ensures building a provisional network sans the involvement of a recognized transportation or an integrated administration. MANETs are usually used for the common usage to emergency situations in warfields, rescue sites etc.
Every node present in MANET can be considered a router. The source node utilizes the intermediate nodes to transmit the message towards the destination node if a source node fails to transmit a message unswervingly to its destination node. MANET networks propose reliability, bandwidth and battery power and have erratic traits like topology. Strength signal and transmission routes. Transmission algorithms and procedures are supposed to be very light to save energy and bandwidth in computation and storage necessities [1, 2, 3, 4, and 5].
Author : Associate professor, Madina Engineering college, kadapa, India. Telephone: 919441112010, E-mail : [email protected] Author : Dr.M.V Subramanyam Ph.D, Principal, Santhi ram Engineering College, Nandyal, Kurnool Dist, A.P, India. Telephone: 919440352909 E-mail : [email protected] Routing information discovery is crucial for all MANET networks using standards such as dynamic source routing (DSR), ad hoc on demand distance vector (AODV), zone routing protocol (ZRP) and location aided routing (LAR) employ the procedure of transmission to launch routes, which can be achieved through the process of data transmission where sender sends a data packet to rest all branches present in MANET. Node mobility and limited system reserves pose serious issues in broadcasting MANETs as compared to wired networks.
2. II.
3. RELATED WORK
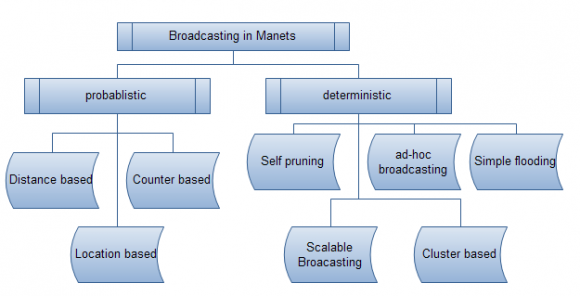
Transmission standards have been categorized into 4 groups namely simple flooding, probability-based methods, area-based methods and neighbor knowledge based methods, in accordance with the fact that the branches should be in order so as to be implemented by Williams and Camp. Simple flooding involves forwarding received data packets by branches one at a time resulting in jamming of network. Probability related methodologies are typically appraised time and again whenever a packet reaches the destination node which happens with some specific probability. When some extra topographical locations are covered due to some emission process, then re-transmission can be expected where area and location related methods explain whether the facades or the span of the projected area is low or not and if yes, then the message is not resent.
GPS or estimation by the triangulation procedure or calculation of power of radio signals hold basis for provision of network information. SBA, Flooding With Self-Pruning (FSWP), AHBP, Multi-point Relaying, etc are few neighbor knowledge related procedures which are essential to procure information of neighborhood neighbors like FWSP uses 1-hop neighbors, SBA, Multipoint Relaying and AHBP uses 2hops neighbors etc. They comprise the last category of transmission methodologies which are again segregated into 2 sub-divisions: neighbor-designating and self-pruning methods whose standard procedure themselves take a decision whether to retransmit the message or not while the former functions by activating its fellows wich are ready to relay a packet.
Stojmenovic and Wu introduced some classifications for transmitting standards which are dependent on their algorithmic nature or the data that is essential for its implementation (network information, the network are taken into consideration. Probabilistic schemes and area-based methods are almost always risky to rely upon due to the fact that they usually fail in terms of randomness and heuristics, respectively.
Wu and Lou introduced a concept stating the quantity of data needed for transmission and also classified standards based on whether they depend on areas including global, quasi-global, local or quasi-local knowledge of the prevalent network wherein global and quasi-global transmitting algorithms are known as centralized standards whose main disadvantage is they are not scalable and hence can be utilized in MANETs. There are few localized standards whose examples are 1 and 2-hops neighborhood standards whose network status information and its topology are exchanged between various branches which is transmitted either by some random "hello" message or transmitted messages whose data content lays down a grave collision on the network throughput ultimately. ? Messages are distributed to all the neighboring nodes by a source node in MANET, the nodes will scan and check whether they have already seen the transmitted message and if yes, the packet is discarded and if not, t will again be re-initiated to all the potential nodes until the message reaches to every node present in the network. This methodology poses the issue of network jamming and weakening of battery power due to the presence of low concentration of nodes and high mobile power. If the messages constitute a polynomial number whose magnitude is (n2), it is of size n and is portrayed in the above diagram.
The topology of the prevalent network designs options for retransmitting of nodes based on probability standards.
? Probability Based Approach: This concept helps to identify and rectify the issues created due to the application of simple flooding methodology. A fixed probability pi for retransmission is assigned for each node I 2 N which involves lessening of the jamming circumstance and avoiding collisions. In situations when pi=1, then this concept turns itself towards simple flooding concept. There is a sufficient decrease in pi if there exists efficient transmission because of the increase and reduction in the count of neighbor density nodes. ? Counter-Based Scheme Approach: The random assessment delay (RAD) is posted, a threshold K is resolved and a counter k >= 1 is fixed on the basis of the count of the received transmitted message which in due course of RAD is increased considerably by one for every acknowledged message. The message is declined when RAD terminates and k >= 1. Few nodes won't be permitted to re-transmit in an opaque MANET while in a less intense MANET, all nodes will retransmit the messages. An area related common broadcasting span is presumed and a node retransmits the message if there is a provision of adequate coverage location. Span and area based approaches are included in the methodologies mentioned below which can be explained as follows:
Distance Based Approach: The counter is made use of in the counter based approach to decline or retransmit a message wherein here, the span concerning the source and the destination node will be chosen by them both, say suppose the span is d. if the value of d is small, the retransmitting coverage span is less and if d is large enough, then the coverage will also be large but if d=0, then the coverage value is 0. The threshold span D is established by a receiving nodule and then RAD is preset where superfluous messages will be preserved until RAD is terminated. Now if d<D, then received transmitted messages will be declined else they'll be retransmitted again. It has been proposed by Ni et al that signal strengths are made use of to estimate the span starting from the source nodule. Span is capable enough to restore signal power by handling the signal threshold. first deemed and extra coverage span is estimated where the message is declined in case RAD terminates when span area is considerably less than the given threshold. The price of estimating extra coverage spans, Location Based Approach: This is concerned with every nodule covering the basic need of instituting self sites for calculating extra coverage more clearly which is based on the global positioning system (GPS). Every node in MANET takes care in attaching its self area to the header part of every message that it is sending or retransmitting. The location of the sender is also considering estimations of intersections among circles is a setback for this approach which can consume the inadequate energy currently available.
Neighborhood based: Status that is prevalent in the neighborhood is managed by the same method wherein matter received from the fellow nodes is employed for retransmission.
Self Pruning: Every node present in this feature is supposed to be aware of who its neighbors are, which can be attained by episodic messages. The receiving nodule evaluates with the source's list as to who all its neighbors are and may retransmit if extra nodes are within reach, else they will al be declined. Figure below depicts retransmission of message from node 2 to node 1 which retransmits them to node 3 and 4 respectively as they are extra nodes and so does node 5 with node 4. Idleness is rampant here even under such circumstances.
? Scalable Broadcasting Approach: Self pruning is enhanced here as there exist higher opportunities for message broadcasting later and also is supposed to make sure that all nodes present in the network are aware of their neighbors until the 2 hop span as each and every node in this methodology consists of a two-hop topology information, which is instituted by "Hello" messages. ? Ad Hoc Broadcasting Approach: This methodology permits only nodules chosen as gateway nodules and a transmission message controller to retransmit the message. It can be explained in detail as follows:
1. Choose one hop fellow nodule as gateway from amongst all the two hop neighboring nodes that can be accessible to a one hop fellow node. 2. Estimate cover set which receives message from the presently in use gateway set. 3. Chose and fix a one hop fellow node as gateway which can cover almost every two hp neighbor that's not present in the cover set. 4. Continue the above processes 2 and 3 till all two hop fellow nodules are enclosed. 5. The nodule which receives a message and is known to be a gateway, decides on which of its fellow nodules have already accepted delivery of the message, they are then presumed to be covered and is declined by the fellow nodule to chose the subsequent hop gateways.
c) Cluster Based Broadcasting Methods Data traffic organization schemas, routing severities, fault tolerance problems are few topics of concern for which clustering approach is considered.
For enlightening its existence, every nodule sends timely "Hello" messages and possesses an exclusive ID. A group of nodes is collectively known as a cluster which can be fashioned as follows: A nodule possessing a restricted negligible IT will nominate self as the cluster in-charge within where a gateway is utilized for transmission between two members of different clusters. In case the two in-charge heads come together, the nodule with the bigger ID status sacrifices its head position. Cluster configuration can be portrayed as follows:
X is a gateway here while Y is the in-charge head.
4. d) Tree Based broadcasting Methods
This methodology is usually not preferable and termed as unsuitable for MANETs even though transmission with the help of tree techniques in wired networks is a famous and technique that is in use too often as they portray a drastic and a powerful transformation in network topologies.
5. e) Technical challenges
This segment focuses on few issues of importance that are to be tackled during the tenure of outlining transmission standards.
6. January 2012 f) Hidden and exposed node problems
This issue is of a major concern during transmission as it renders the transport of nodes to all locations unfeasible concerning a given phase of network subsets. This is supposed to be rectified by the usage of acknowledgement packets (ACKs) but this would be against the rule of transmission that specifies to reduce the count of data packet production. Subsequently, the main principle of transmission within a static ad hoc network is to avail to as many nodes that are within reach. A transmitting standard may be unsuccessful even at the slightest hint of non-availability of acknowledgement packets.
7. g) Mobility and Partitioning
Mobility is another important issue of concern, the transmitting standards are supposed to face.
Transmission of messages on the basis of spanning trees endures problems posed by the mobility factor, which can now be dealt with expertly because of the availability of many equipped algorithms that are competent enough. These methodologies also are not specific on which application they want to work with. Hence, considering transmission tends to give an idea as to how the corresponding spanning tree is supposed to be built, which is done by exploring group of relevant nodes that have already been recipients of the sender.
This issue in static ad hoc networks can also unwillingly pave way to separated networks which is another issue of major concern, taking broadcasting in particular. A transmitting standard is supposed to be searching evidently for a methodology which can permit a transmitting message to leap to various subsets, so as to cover as many nodules as it is permitted. Epidemic dispersive replicas can be correlated with this concern.
8. h) Frequently cited broadcasting methods literature
The cluster that materializes in MANET is supposed to be preserved on a regular basis as said by Ni et al by the fundamental cluster algorithm. All the remaining nodules in a cluster other than the controlling nodule can be enveloped by the retransmission done by the controller. Gateway nodes are extensively utilized for retransmitting message to other nodules in various clusters and hence there is no extreme necessity of a non-gateway nodule to retransmit the same message. Even though there may be presence of many gateway nodules in various clusters, te specified gateways may probably utilize and employ different transmission concepts mentioned earlier to ascertain whether to retransmit or not.
Spanning trees are widely built though which transmission of messages is done by promoting messages only to the fellow nodules present in the tree which is basically acyclic in nature. Hence, every transmitted message is acquired only once at a time by the prevailing nodes. Many algorithms are available for building and upholding trees like the bridged Ethernet network's spanning tree algorithm which are built to prove suitable for working in stable networks rather than the ever-changing topology of a MANET.
Multicast trees and their uses have already been specified and explained in detail by many authors but what is nagging is the fact their algorithms are not qualified and efficient enough for dealing with the topology related modifications. Few algorithms render their services useless for handling the tree in an everchanging topology even though they may involve a phase of building a spanning tree.
The logic of one-to-one broadcasting is proved feasible by the tree related technique as compared to other methods as many disadvantages of limited transmissions do not influence the algorithm thankfully, it is secure enough for transmissions.
A noteworthy point to mention is there is minimum or no effort required to be at par with the network states as it has been proposed from the start to reduce signaling traffic. i) Current state of the art A multiple channel medium access control (MAC) standard was recommended by Jenhui Chen et al which was named as ad hoc multichannel negotiation protocol (AMNP) used mainly for transmitting messages across multiple channels in a uniform manner and also referred to the problem of distributed scheme allowance for multihop MANETs but in the presence of one transceiver. Augmentation of description of AMNP known as AMNP with channel development was brought into existence.
The replication results prove worthy to make its stand that the throughput is comparatively large in comparison to its single path equivalent. Only a single transceiver is deployed by the recommended AMNP but with a specified constraint of suspending right to admission for a specific time period while getting swapped to a chosen data route.
It has been suggested by Chien-Chung Shen et al, a diagram-prospect related directional to curve percolation and also for omni-directional transmission for spot percolation and also gives a detailed explanation about the compilation of directional transmitter related transmission methods for static ad hoc networks. The author squabbles to support the stipulation of suggested copy, that countless transmission designs have been recommended almost all of which presumed the practice of omni-directional transmitters and transmission overhead is taken into consideration advancing number of dispatching nodules. Directional transmitters possess tapered emissions and can gradually diminish transmission overheard with respect to number of acknowledged packets to the count of nodules that expects transmission packets.
Observation: It has been suggested that diagram-prospect related directional to curve percolation and also for omni-directional transmission for spot percolation and also gives a detailed explanation about the compilation of directional transmitter related transmission methods for static ad hoc networks. A specific quantity of battery power is safeguarded by decreasing the count of replica of data packets that is acknowledged. For utilizing the longer range characteristics of directional transmitters for deceasing the delay, it is but essential to scrutinize the recommended ideas.
Transmission storm issue would be a troubling factor if the accelerating nodules are not cautiously allocated in the transmission procedure in static ad hoc networks (MANETs) said Wei Lou et al. The main idea behind diminishing transmission idleness is a foremost issue of concern in MANETs and so an easy transmission algorithm has been recommended known as double-covered broadcast (DCB), which benefits from the transmission idleness state for enhancing delivery ratio in a high broadcasting error rate surrounding subset.
Few chosen promoting nodules rebroadcast the transmitted message from among the 1-hop fellow nodules pertaining to the sender. The above mentioned nodules are chosen as follows:
1) 2-hop fellow nodules of the source initiator are swathed and 2) The source initiator's 1-hop fellow nodules are either advancing nodules or non advancing ones that are enveloped by a minimum of two promoting fellow nodules.
The source initiator acquires hold of the rebroadcasts of the promoting nodules as authentication of reaction of the data packet. The non promoting 1-hop fellow nodules of the source initiator fail to admit the response reaction of their transmission which provokes the initiator to retransmit the data packet in case of it failing to recognize all the promoting nodules broadcast till large count of retries has been reached.
Observation: Suppose in DCB, a nodule v promotes a data packet choosing division of the prevalent 1-hop fellow nodules as promoting nodules depending on the greedy algorithm for the issue pertaining to Set Cover with certain restrictions which are as follows: (1) All the 2-hop fellow nodules of node v are supposed to be addressed by the chosen advancing nodes and (2) the 1-hop fellow nodules available in node v can either be chosen as an advancing nodule r enveloped by a minimum of two promoting nodes. Then, the IDs of the chosen promoting nodules to the relevant data packet is appended to the node v and then the same packet is transmitted. It is assumed beforehand by a 1-hop fellow node that the about-to-be received data packet is of a promoting nature and transmission procedure continues as it was before concerning node v. Another noteworthy characteristic of DCB is that whenever a nodule tends to broadcast a packet secure connections are ensured. Node v delays time to eavesdrop on transmission from all its chosen promoting nodules and if it falls short for the same, then rebroadcasting is permitted until all nodules are swathed and maximum tries are attained.
9. j) Limits and obstacles observed in Existing
Broadcasting Methods
The disadvantages construed from itemizing relative studies are as follows:
1. There is a need for many retransmissions concerning with the count of the rebroadcasting nodules for all methodologies explained except for the neighbor related techniques.
2. RAD implemented techniques drowned in high density MANETs acclimatize RAD nodules concerning its surrounding conduct is cultivated.
10. The ad hoc transmitting technique faces
discrepancies in a typically high static MANET network because of the fact that it fails to make use of local data to confirm whether to retransmit the packet or not.
On the basis of the wide proportional research on already existing transmitting techniques, it has been observed that every transmitting technique failed to work in wide ranging MANET surroundings.
Scalable transmission based line of attack has provided with noteworthy and promising results as compared to the non-adaptive tactics.
There is an urgent need to cultivate new competent data transmission tactics with the main intention of preserving the existing meager reserves in MANETs.
11. VII.
12. CONCLUSION
Transmission is an indispensible feature for any MANET network, so it is vital to exploit the most proficient transmitting techniques that can make sure that a secure network is provisioned. This paper also has presented a brief synopsis on all chief transmission methodologies available in the prose, mainly concentrating on the intricacies of their roles and also the threats posed by them and also, recommending upgrading for few of the enumerated techniques. There is not one most favorable algorithm in existence for all the concerning techniques in the present circumstances