1. Introduction
n Artificial Neural Network (ANN) is an information processing paradigm that is inspired by the way biological nervous systems, such as the brain, process An ANN is configured for a specific application, such as pattern recognition or data classification, through a learning process [12]. Learning in biological systems involves adjustments to the synaptic connections that exist between the neurons. [12]Cryptosystems are commonly used for protecting the integrity, confidentiality, and authenticity of information resources. In addition to meeting standard specifications relating to encryption and decryption, such systems must meet increasingly stringent specifications concerning information security. This is mostly due to the steady demand to protect data and resources from disclosure, to guarantee the authenticity of data, and to protect systems from web based attacks. For these reasons, the development and evaluation of cryptographic algorithms is a challenging task.
This paper is an investigation of using ANN based n-state sequential machine and chaotic neural network in the field of cryptography .the rest of the paper is organized as follows: section 2 discusses background and related work in the field of ANN based cryptography, section 3 proposed method related to nstate sequential machine and chaotic neural network section 4 discusses implementation section 5 discusses experimental report and test result and finally section 6 discusses conclusion.
2. II.
Background and related work Jason L. Wright , Milos Manic Proposed a research paper on Neural Network Approach to Locating Cryptography in Object Code. In this paper, artificial neural networks are used to classify functional blocks from a disassembled program as being either cryptography related or not. The resulting system, referred to as NNLC (Neural Net for Locating Cryptography) is presented and results of applying this system to various libraries are described [ 2].
John Justin M, Manimurugan S introduced A Survey on Various Encryption Techniques. This paper focuses mainly on the different kinds of encryption techniques that are existing, and framing all the techniques together as a literature survey. Aim an extensive experimental study of implementations of various available encryption techniques. Also focuses on image encryption techniques, information encryption techniques, double encryption and Chaos-based encryption techniques. This study extends to the performance parameters used in encryption processes and analysing on their security issues [3].
Ilker DALKIRAN, Kenan DANIS¸MAN introduced a research paper on Artificial neural network based chaotic generator for cryptology . In this paper, to overcome disadvantages of chaotic systems, the dynamics of Chua's circuit namely x, y and z were modeled using Artificial Neural Network (ANN). ANNs have some distinctive capabilities like learning from experiences, generalizing from a few data and nonlinear relationship between inputs and outputs. The proposed ANN was trained in diffrent structures using different learning algorithms. To train the ANN, 24 different sets including the initial conditions of Chua's circuit were used and each set consisted of about 1800 input-output data. The experimental results showed that a feed-forward Multi Layer Perceptron (MLP), trained with Bayesian Regulation back propagation algorithm, was found as the suitable network structure. As a case study, a message was first encrypted and then decrypted by the chaotic dynamics obtained from the proposed ANN and a comparison was made between the proposed ANN and the numerical solution of Chua's circuit about encrypted and decrypted messages [5].
Eva Volna ,Martin Kotyrba ,Vaclav Kocian, Michal Janosek developed a Cryptography Based on Neural Network. This paper deals with using neural network in cryptography, e.g. designing such neural network that would be practically used in the area of cryptography. This paper also includes an experimental demonstration [6].
Karam M. Z. Othman , Mohammed H. Al Jammas Introduced Implementation of Neural -Cryptographic System Using Fpga. In this work, a Pseudo Random Number Generator (PRNG) based on artificial Neural Networks (ANN) has been designed. This PRNG has been used to design stream cipher system with high statistical randomness properties of its key sequence using ANN. Software simulation has been build using MATLAB to firstly, ensure passing four wellknown statistical tests that guaranteed randomness characteristics. Secondly, such stream cipher system is required to be implemented using FPGA technology, therefore, minimum hardware requirements has to be considered [7].
T. Schmidt , H. Rahnama Developed A Review of Applications of Artificial Neural Networks In Cryptosystems. This paper presents a review of the literature on the use of artificial neutral networks in cryptography. Different neural network based approaches have been categorized based on their applications to different components of cryptosystems such as secret key protocols, visual cryptography, design of random generators, digital watermarking, and steganalysis [8].
Wenwu Yu, Jinde Cao introduced Cryptography based on delayed chaotic neural networks. In this Letter, a novel approach of encryption based on chaotic Hopfield neural networks with time varying delay is proposed. We use the chaotic neural network to generate binary sequences which will be used for masking plaintext. The plaintext is masked by switching of chaotic neural network maps and permutation of generated binary sequences. Simulation results were given to show the feasibility and effectiveness in the proposed scheme of this Letter. As a result, chaotic cryptography becomes more practical in the secure transmission of large multi-media files over public data communication network [9] III.
3. PROPOSED METHOD
A number of studies have already investigated different machine learning methodologies, specifically neural networks and their applications in cryptography, but It is uncommon technique to using Artificial Neural network based n-state sequential machine and Chaotic neural network in the field of cryptography .
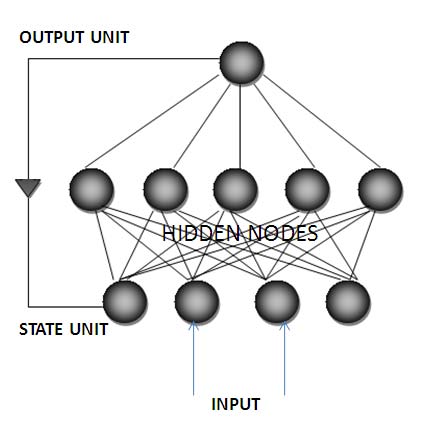
4. a) Sequential Machine
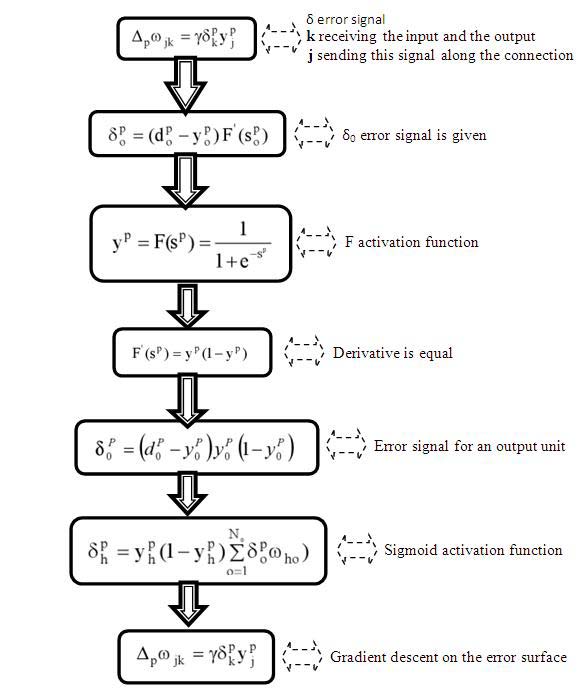
A sequential Machine output depends on state of the machine as well as the input given to the sequential machine. Therefore Michel I .Jordan Network was designed because in which output are treated as input. We are used these type of input as a state. As a sequential machine can be achieved by using a Michel I. Jordan neural network, therefore data are successfully encrypted and decrypted. In this case the starting state of the n-state sequential machine can act as a key. Data is used to train the neural network as it provides the way the machine moves from one state to another. c) Cryptography Achieved by a chaotic neural network Cryptography scheme was done by a chaotic neural network. A network is called chaotic neural network if its weights and biases are determined by chaotic sequence. Specially encryption of digital signal we used chaotic neural network. The reason for using sequential machine for implementation is that the output and input can have any type of relationship and the output depends on the starting state. The starting state is used as a key for encryption and decryption. If the starting state is not known, it is not possible to retrieve the data by decryption even if the state table or the working of the sequential state is known. For training of the neural network, any type of sequential machine can be used with the key showing the complexity or the level of security obtained.
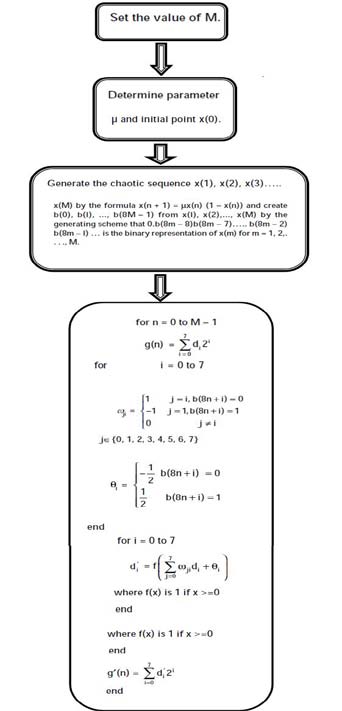
5. c) Cryptography Achieved Through chaotic neural network
A chaotic neural network in which weights and biases are determined by a chaotic sequence. g = digital signal of length M and g (n) 0 ? M-1 , be the one-byte value of the signal g at position n .The decryption procedure is the same as the above one except that the input signal to the decryption Chaotic neural network should be g'(n) and its output signal should be g"(n).
V.
6. Experiment and test result a) Sequential Machine
A general n-state Sequential Machine was implemented. As an example, the serial adder was implemented using this machine. There is initial state is informed to the user for the input bits to be added. The output is the sum and the carry bit. After that the execution of program has been completed it is automatically jumps to the new carry state. This output is considered as previous carry state.
Following Graph illustrate Mean Square Error when we Enter input 0,1 and 2 .we apply this input in two feed forward Adder One is of Multilayer single output feed forward Adder and other is Multilayer multiple output feed forward Adder.
First we apply Input Number 0,1 and 2 on Multilayer single output feed forward and find MSE on Linear scale . Year and generated encrypted letter similarly is the starting state is 1 the letter is shifted by 2.The state is automatically move to next state .If the next input is again A the output will be C as the current state now is 1. For H, state 0 will flip the letter to A while state 1 will flip the output to B. This method can be used to encrypt a word containing only the letters A to H.

| Conditions (Values of x(0) and µ()) | ||||
| Same Input Encrypted with Different Initial Conditions | ||||
| (Values of x(0) and µ()) | ||||
| Output with | Output with | output with | ||
| ASCII | x(0)= 0.75 | x(0)= 0.85 | x(0)= 0.90 | |
| INPUT | CODE | µ=3.9 | µ=3.5 | µ=3.2 |
| A | 97 | 199 | 233 | 204 |
| B | 98 | 195 | 112 | 98 |
| C | 99 | 200 | 239 | 11 |
| D | 100 | 253 | 108 | 31 |
| E | 101 | 220 | 226 | 1 |
| F | 102 | 17 | 115 | 25 |
| G | 103 | 187 | 234 | 56 |
| H | 104 | 101 | 109 | 235 |
| I | 105 | 6 | 236 | 49 |
| J | 106 | 138 | 115 | 226 |
| K | 107 | 107 | 229 | 36 |
| L | 108 | 32 | 110 | 225 |
| M | 109 | 180 | 238 | 42 |
| N | 110 | 119 | 112 | 254 |
| O | 111 | 225 | 224 | 45 |
| P | 112 | 184 | 113 | 225 |
| Q | 113 | 63 | 243 | 49 |
| R | 114 | 168 | 83 | 227 |
| S | 115 | 103 | 252 | 51 |
| T | 116 | 245 | 116 | 229 |
| U | 117 | 160 | 244 | 53 |
| V | 118 | 83 | 84 | 231 |
| W | 119 | 209 | 248 | 55 |
| X | 120 | 219 | 120 | 233 |
| Y | 121 | 209 | 248 | 57 |
| Z | 122 | 231 | 88 | 235 |
| Decrypted Using Same and Different Initial Conditions | |||||
| Encrypted Data of Table 1 (Column 2) Decrypted Using | |||||
| Same and Different Initial Conditions | |||||
| Output Obtained Using | Output Obtained Using | ||||
| Same Initial Condition | Different Initial Condition | ||||
| output with | output with | output with | |||
| ASCII | x(0)= 0.75 | x(0)= 0.85 | x(0)= 0.90 | ||
| INPUT | CODE | µ=3.9 | µ=3.5 | µ=3.2 | |
| A | 199 | 97 | 79 | 106 | |
| B | 195 | 98 | 209 | 195 | |
| C | 200 | 99 | 68 | 160 | |
| D | 253 | 100 | 245 | 134 | |
| E | 220 | 101 | 91 | 184 | |
| F | 17 | 102 | 4 | 110 | |
| G | 187 | 103 | 54 | 228 | |
| H | 101 | 104 | 96 | 230 | |
| I | 6 | 105 | 131 | 94 | |
| J | 138 | 106 | 147 | 2 | |
| K | 107 | 107 | 229 | 36 | |
| L | 32 | 108 | 34 | 173 | |
| M | 180 | 109 | 55 | 243 | |
| N | 119 | 110 | 105 | 231 | |
| O | 225 | 111 | 110 | 163 | |
| P | 184 | 112 | 185 | 41 | |
| Q | 63 | 113 | 189 | 127 | |
| R | 168 | 114 | 137 | 57 | |
| S | 103 | 115 | 232 | 39 | |
| T U | 245 160 | 116 117 | 245 33 | 100 224 | ( D D D D ) D |
| V | 83 | 118 | 113 | 194 | |
| W | 209 | 119 | 94 | 145 | |
| X | 219 | 120 | 219 | 74 | |
| Y | 209 | 121 | 80 | 145 | |
| Z | 231 | 122 | 197 | 118 | |
| Decrypted Using Same and Different Initial Conditions | ||||
| Encrypted Data of Table 1 (Column 3) Decrypted Using | ||||
| Same and Different Initial Conditions | ||||
| Output Obtained Using | Output Obtained Using | |||
| Same Initial Condition | Different Initial Condition | |||
| output with | output with | output with | ||
| ASCII | x(0)= 0.75 | x(0)= 0.85 | x(0)= 0.90 | |
| INPUT | CODE | µ=3.9 | µ=3.5 | µ=3.2 |
| A | 233 | 79 | 97 | 68 |
| B | 112 | 209 | 98 | 112 |
| C | 239 | 68 | 99 | 135 |
| D | 108 | 245 | 100 | 23 |
| E | 226 | 91 | 101 | 134 |
| F | 115 | 4 | 102 | 12 |
| G | 234 | 54 | 103 | 181 |
| H | 109 | 96 | 104 | 238 |
| I | 236 | 131 | 105 | 180 |
| J | 115 | 147 | 106 | 251 |
| K | 229 | 229 | 107 | 170 |
| L | 110 | 34 | 108 | 227 |
| M | 238 | 55 | 109 | 169 |
| N | 112 | 105 | 110 | 224 |
| O | 224 | 110 | 111 | 162 |
| P | 113 | 185 | 112 | 224 |
| Q | 243 | 189 | 113 | 179 |
| R | 83 | 137 | 114 | 194 |
| S | 252 | 232 | 115 | 188 |
| T | 116 | 245 | 116 | 229 |
| U | 244 | 33 | 117 | 180 |
| V | 84 | 113 | 118 | 197 |
| W | 248 | 94 | 119 | 184 |
| X | 120 | 219 | 120 | 233 |
| Y | 248 | 80 | 121 | 184 |
| Z | 88 | 197 | 122 | 201 |
| Decrypted Using Same and Different Initial Conditions | |||||
| Encrypted Data of Table 1 (Column 4) Decrypted Using | |||||
| Same and Different Initial Conditions | |||||
| Output Obtained Using | Output Obtained Using | ||||
| Same Initial Condition | Different Initial Condition | ||||
| output with | output with | ||||
| ASCII | x(0)= 0.75 | x(0)= 0.85 | output with x(0)= | ||
| INPUT | CODE | µ=3.9 | µ=3.5 | 0.90 µ=3.2 | |
| A | 204 | 106 | 68 | 97 | |
| B | 98 | 195 | 112 | 98 | |
| C | 11 | 160 | 135 | 99 | |
| D | 31 | 134 | 23 | 100 | |
| E | 1 | 184 | 134 | 101 | |
| F | 25 | 110 | 12 | 102 | |
| G | 56 | 228 | 181 | 103 | |
| H | 235 | 230 | 238 | 104 | |
| I | 49 | 94 | 180 | 105 | |
| J | 226 | 2 | 251 | 106 | |
| K | 36 | 36 | 170 | 107 | |
| L | 225 | 173 | 227 | 108 | |
| M | 42 | 243 | 169 | 109 | |
| N | 254 | 231 | 224 | 110 | |
| O | 45 | 163 | 162 | 111 | |
| P | 225 | 41 | 224 | 112 | |
| Q | 49 | 127 | 179 | 113 | |
| R | 227 | 57 | 194 | 114 | |
| S | 51 | 39 | 188 | 115 | |
| T | 229 | 100 | 229 | 116 | |
| U | 53 | 224 | 180 | 117 | |
| V | 231 | 194 | 197 | 118 | |
| W | 55 | 145 | 184 | 119 | |
| X | 233 | 74 | 233 | 120 | |
| Y | 57 | 145 | 184 | 121 | |
| Z | 235 | 118 | 201 | 122 | |
| It is clear from table 2, 3 and 4 that we can | |||||
| decrypt an encrypted data correctly by knowing the | |||||
| exact values of | x (0) and µ otherwise we get the | ||||
| wrong data as shown in table 2,3 and 4. | |||||
| VI. | Conclusion | ||||